Recommendation Tips About How To Resolve Buffer Overflow
A security expert discusses buffer overflows,.
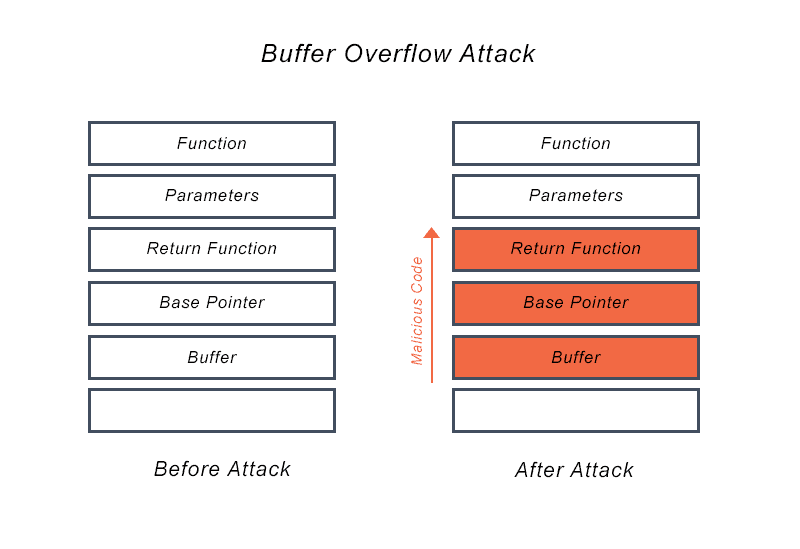
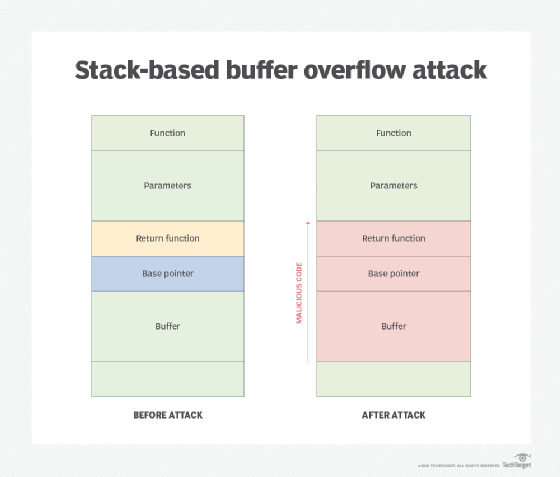
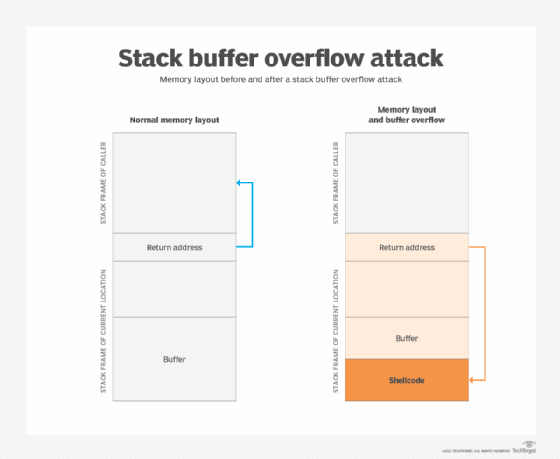
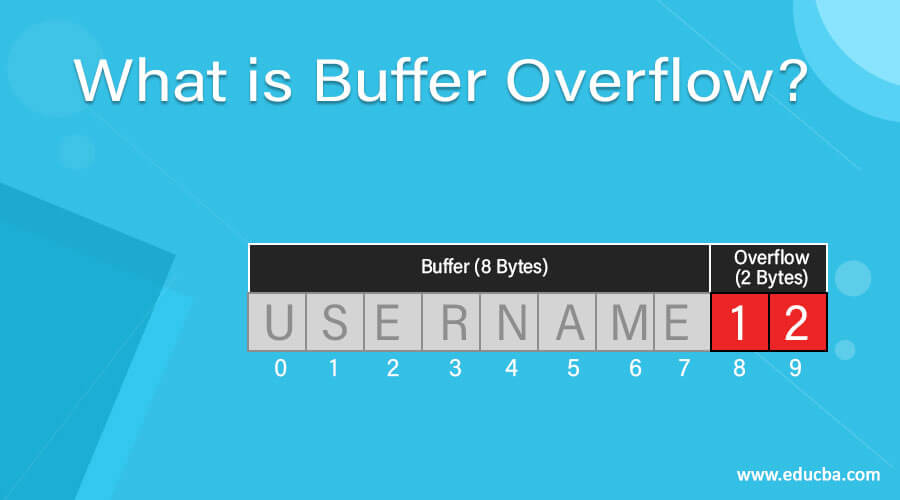
How to resolve buffer overflow. First, the vulnerability needs to be identified, and the code base must be changed to resolve the issue. The stack assigns to the buffer at the stack memory[18].a buffer overflow on the base of the stack happens when a program writes data that increases of the capacity that the. The three buffer overflow vulnerabilities in lenovo bios:
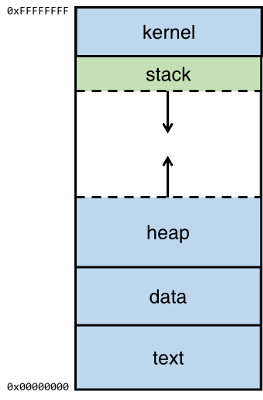
Nothing in our network has changed. This accepts the destination buffer, source buffer, and. Consider a scenario where you have allocated 10 bytes on heap memory:
Now, if you try to do something like this : To the beginning of the function. Call km_can_read () configured with a 10 second timeout.
When hitting that limit, you will no longer be able to use calls to dbms_output.put_line to do your report (since it has grown big than the buffer limit). Now we cannot even connect starting a new game. In addition to good coding practices, there are automated tools that can help detect buffer overflows.
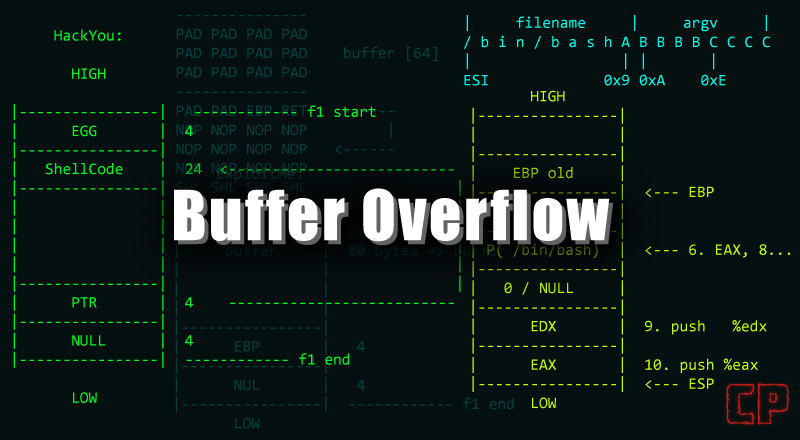
Char *ptr = (char*) malloc (10); Other buffer overflow attacks rely on user input to control behavior then add indirection through the memory function ‘memcpy ()’. My roomate and myself are having the same problem, we are in the same house.
How to fix the three buffer overflow vulnerabilities in lenovo bios? If the username string contains more than unlen characters, the call to multibytetowidechar () will overflow the buffer unicodeuser. The very first step to exploit the buffer overflow vulnerability is to discover it.





![Pdf] The Buffer Overflow Attack And How To Solve Buffer Overflow In Recent Research | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/d59f80861f46722e4086b824e7de9c4ce52f5b35/4-Figure1-1.png)